It’s been a while since I last done a write up of an investigation I’ve done on LetsDefend. My time lately has been taken up by building home lab environments and completing various challenges on LetsDefend.
I should be in a position to complete some write ups and reports detailing my work on the home labs soon.
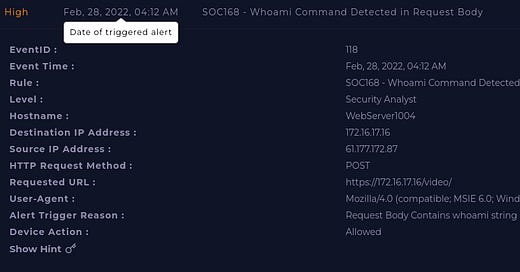
I decided to write up Event ID 118 (SOC 168 - Whoami Command Detected in Request Body).
As the ticket suggests an alert has been triggered due to the “whoami” command appearing within the body of the request.
So, lets take a look at the playbook.
From the alert above the 2 IP addresses of interest are 61[.]177[.]172[.]87 and 172[.]16[.]17[.]16. (WebServer 1004)
Taking the unknown IP address and analysing it on VirusTotal, the result returns as malicious. Originating from China.
Time to examine the traffic. A simple review of the logs, searching for the malicious IP Address 61[.]177[.]172[.]87 retrieves 5 log entries.


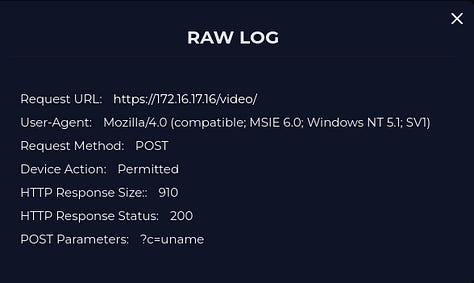


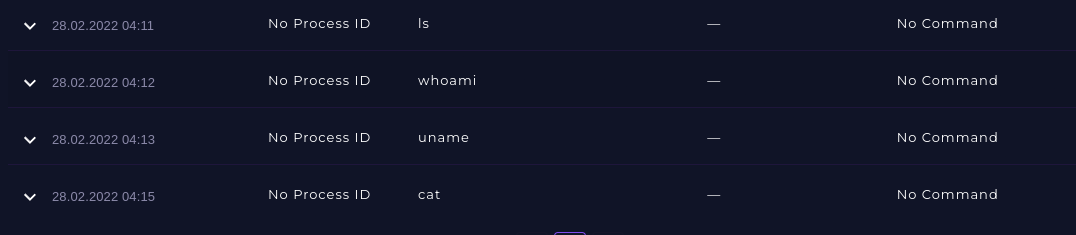
Looking at them chronologically. What is concerning is every request returned a HTTP Response Status of “200”, indicating success. I did highlight the particular areas of concern but for some reason Substack kept taking me offline when I listed them. You can still see from the Post Parameters in the images above what commands were injected.
Reviewing the logs on the WebServer, the commands are displayed indicating they were executed successfully.
From analysing the network logs, there were only 5 entries related to the malicious IP Address.
Clearly from the investigation so far, we can conclude that the traffic is in fact malicious.
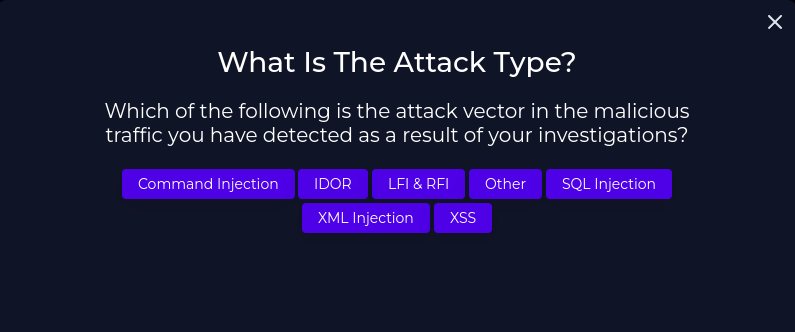
If we look closely at the raw logs from previous, it is a Command Injection attack.
I searched around the email security section of the SIEM for any emails relating to either IP address, WebServer1004 and planned testing. There was nothing identifying this to have been a planned test.
As the traffic is not part of the Company Network, the direction of traffic is from the Internet → Company Network
As already confirmed from 2 sources, the attack was successful. The final step before producing a report is to isolate the affected WebServer from the Network and escalate to a SOC2 analyst to review.
Thanks for reading, I’ll try not to wait so long until the next write up!