SOAR-EDR Project
This is a project created by MyDFIR
SOAR-EDR Project
The aim of this project is to create a Security Orchestration, Automation and Response (SOAR) environment utilising Vultr, LimaCharlie, Tines and Slack.
This project is based on the SOAR-EDR videos by mydfir on YouTube
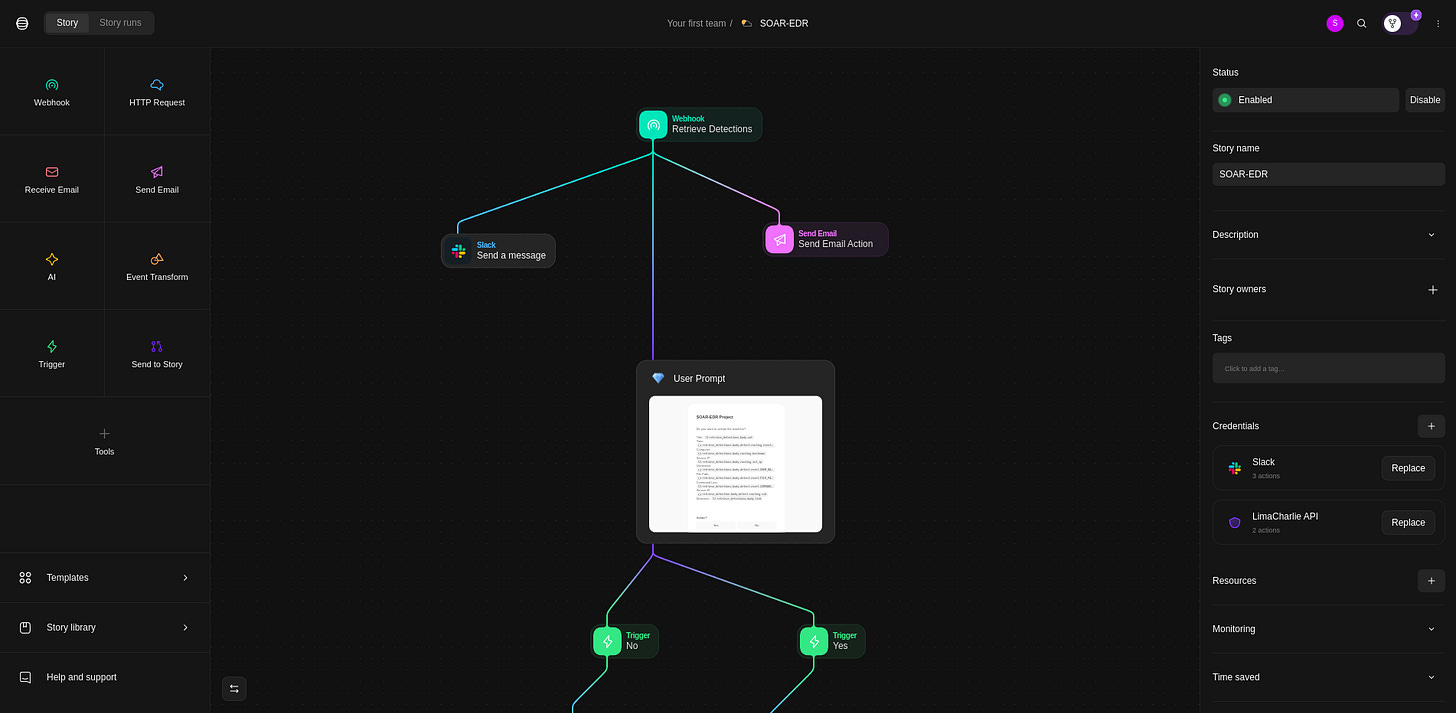
Playbook Workflow
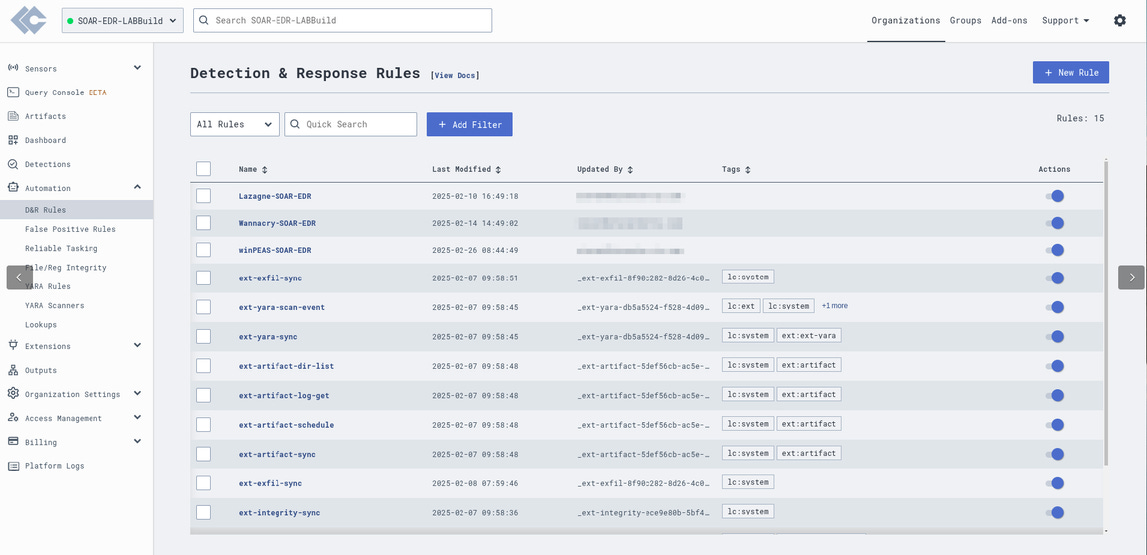
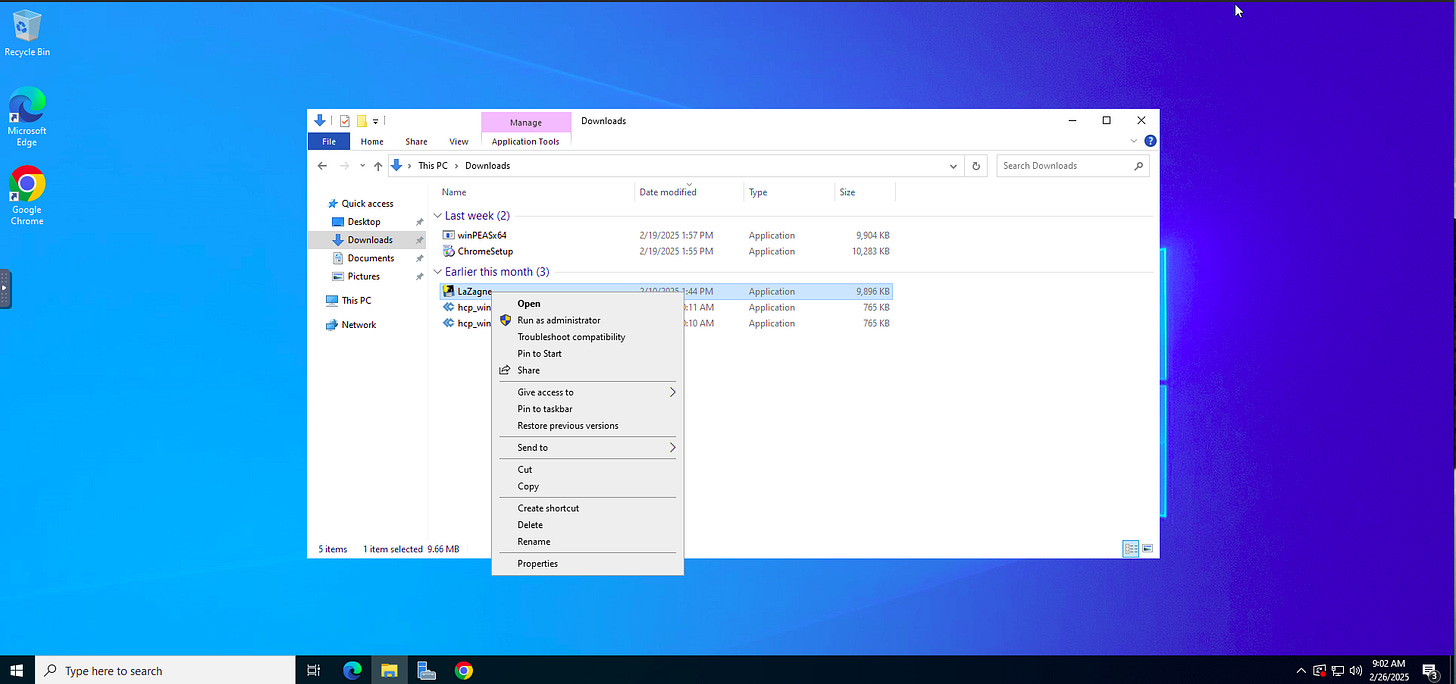
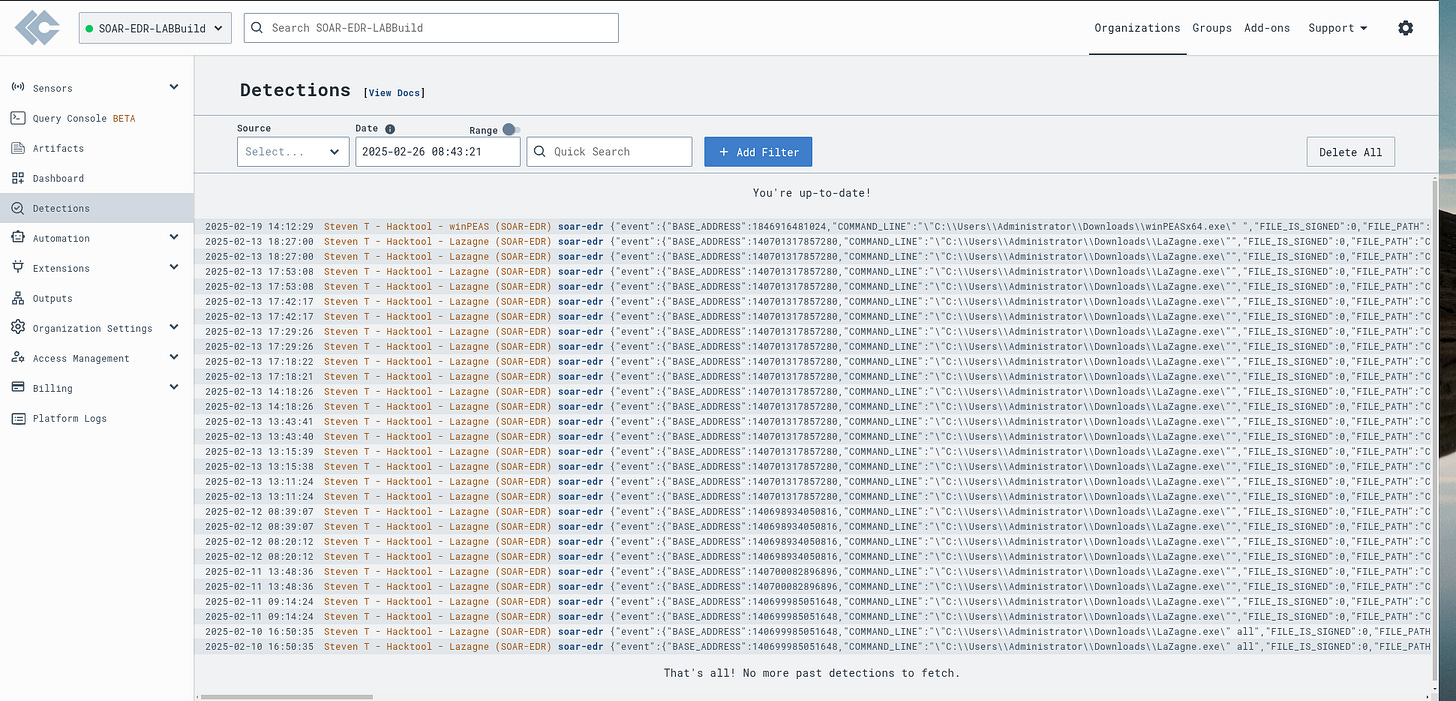
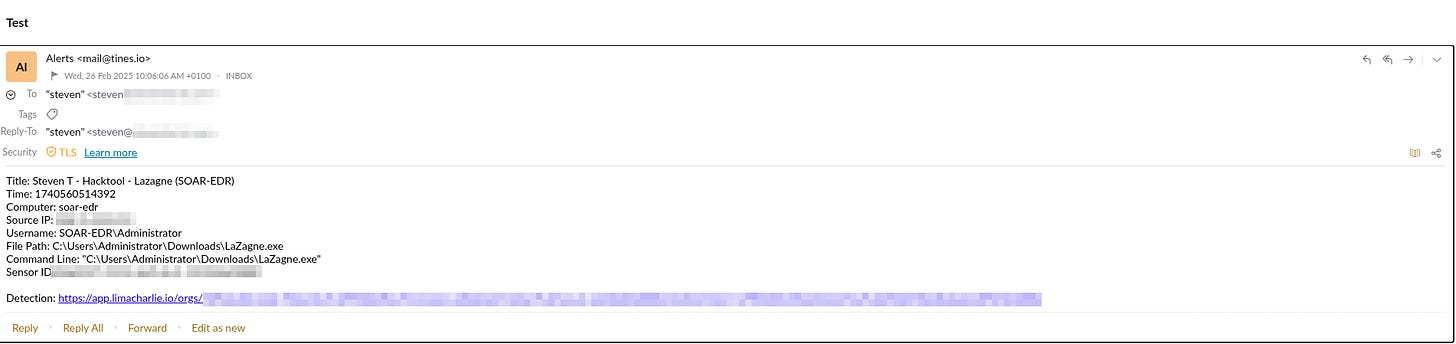
In this project, the aim to set up a SOAR-EDR environment utilising a Windows Server in Vultr’s cloud environment. The server will communicate with LimaCharlie where I will configure a detection and response rule to detect the hacktool. In this project the hacktool will be LaZagne, although to get practice in writing detection rules I also wrote one for winPEAS.exe and Wannacry (this one I didn’t test out).
Upon detection by LimaCharlie, the detection is passed onto Tines to begin the automation process. Tines will forward a message to Slack and also send an email detailing the detection.
The user will be provided the prompt for Yes - Isolate, which will automatically communicate with LimaCharlie and isolate the machine from the network or No - where the machine will not be isolated but the user will be prompted to investigate the alert.
Setting up D+R Rules on LimaCharlie
Setting up Tines Automation
Detection and Automation in Action
Isolation Actions
Review of the Project
Coming into this project I had zero experience or knowledge with using a cloud service, so getting an opportunity to use Vultr to create and deploy a server was beneficial. I also got the opportunity to use Tines and Slack, neither of which I had used previously either.
I really enjoyed the ease of use with Tines in creating the automation workflow although I did have an issue with the LimaCharlie API on it. Often the key used for it would change and I’d have to reconnect it to LimaCharlie. They also have a pretty frustration Captcha which would not accept some of my correct responses and I’d have to go through the process multiple times.
Although I have used LimaCharlie before I learned how to create detection rules and how to tweak existing rules to detect other threats, such as winPEAS. Really like LimaCharlie and how much information it pulls through from the end points and how easy it is to set up and use.
Really enjoyable project overall, so a massive thanks to Steven (MyDFIR on YouTube) for creating this project. By far the best part was watching the automation successfully complete after spending the time putting it all together.