After the buzz from discovering I was successful in passing my PSAA exam (You can read about it here), I made the decision to take the rest of last week off. It was a hectic couple of weeks in preparation for the exam and I just wanted to make sure I was rested, recharged and ready to go again.
So, with confidence high I took on the ‘Python Stealer’ challenge through LetsDefend which is rated as a Hard level of difficulty. The object of this challenge is to analyse the python script and identify the information required to answer the questions.
Q1 - What is the function that is used to decrypt the master key?
To find the answer for this question we need to look at the script and in particular we are looking for information related to defining the decrypt function.
Q2 - What is the mode that is used by the AES algorithm?
This is a pretty straight forward answer, included in the exact same part of the script as Q1.
Q3 - What is the name of the author of the code?
Progressing down the script, we are looking for anything which indicates the author’s name or handle. Possibly something linking back to a repository.
Q4 - What is the UserAgent in the code?
Really straight forward again, this time looking for the ‘User-Agent’ field.
Q5 - What is the hooked URL?
To locate the webhook, we can look for the defined function within the code.
Q6 - What is the name of the function that is used to collect data from the browser?
For this answer, look for the section of code related to various web browsers, and identify the defined function of the code.
Q7 - What is the ID paragraph element that allows an attacker to parse HTML?
Looking through the script, we can see ‘html.parser’ within the code with the #id below it.
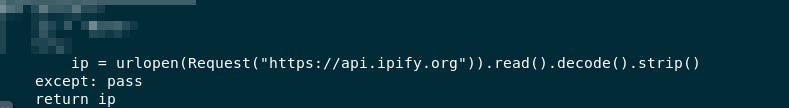
Q8 - What is the function name that is used to retrieve IP addresses?
Looking at the question, we can identify that we are looking for a function being defined, this time related to IP.
Q9 - What is the regex that is used to dump tokens?
Do you know what regex looks like? A simple search online will show you what to be on the lookout for here.
Q10 - What is the avatar_url?
Another easy answer to find. This time looking for ‘avatar_url’ within the code.
Overall, this is a really straight forward challenge. I am no expert in Python but what knowledge I do have probably made this seem really easy, despite it being rated as Hard. If you have never came across python before, you can still have fun with this challenge. The information is all in plain text and it is good to get familure with how the language is written, even if you don’t fully follow the functionality.