This morning I Investigated LetsDefend Event ID 197. This alert relates to a potential zero-day attack on an Atlassian Confluence server.
I’ve got to be honest in saying I had never heard of it before but from what I’ve learned in Cyber Security, you’ll never know everything, so it’s vital to know where to look for more information.
From the initial alert we can identify the alert reason, “Alert Trigger Reason :This activity may be indicative of an attempt to exploit the CVE-2023-22515 vulnerability, which could potentially lead to create a new administrator user.”
BUT what is CVE-2023-22515? Searching for this particular CVE led me to the official website of Atlassian where they provide the summary of the vulnerability as well as information relating to the affected versions as well as information on threat detection and remediation. For more information, click on the link provided.
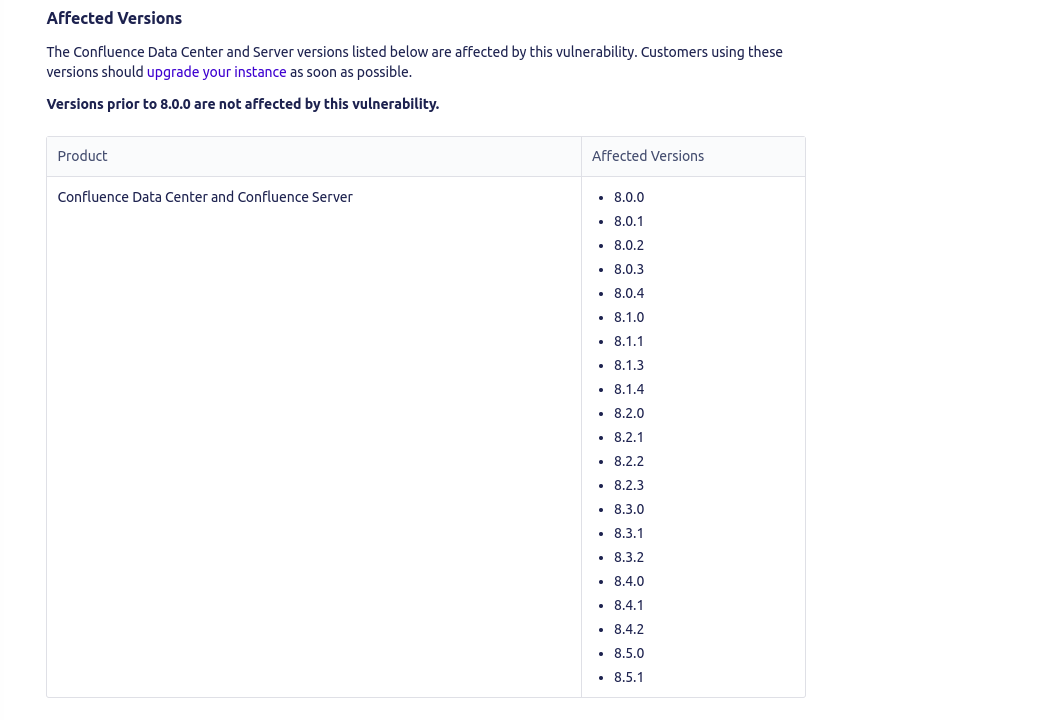
This led me to query what version number was running on our instance to determine whether it is vulnerable to attack.
As displayed in the information above, the server is vulnerable to the zero day attack.
Performing some reputation checks on the source IP Address on VirusTotal, the IP returns with a malicious result originating in the US. The address also returns a malicious result using the Threat Intel tab on the SIEM.
The last part of information gathering we can do is to check the traffic logs between the host and the source ip addresses. Here we can see http traffic on port 80.
So what traffic is present within the logs?
From the Confluence Access Logs, we can see the communication from the attacker to the server. The URL containing “setupadministrator” is concerning as is the proceeding URL containing “finishsetup”.
There are more logs which show “POST” responses with a code of 302 and then 200. These strongly suggest the attacker was successful in their attack on the server, allowing them to create an administrator account.
Given that the administrator account creation is unauthorised, the traffic is clearly malicious.
The attack itself does not fall under any of the categories, therefore must be “Other”
After a search on the email security tab of the SIEM, there is no indication that this is a planned test.
As identified during the information gathering stage, the traffic is external to the network. Therefore it is Internet →Company Network
Based on the logs, the attacker was successful in their attack.
The last steps to take in the playbook are to isolate the server and as the attack was successful, to escalate the case to a Tier 2 analyst to review further.